How to operate quickly and easily logs Windows login?
en:How to operate quickly and easily logs Windows login?
he:כיצד להפעיל בקלות ובמהירות יומני כניסה למערכת של Windows?
ru:Как действовать быстро и легко журналы Windows Логин?
ja:どのように迅速かつ簡単に動作する Windows ログインのログ?
ar:كيف تعمل بسرعة وسهولة تسجيل دخول Windows؟
zh:如何操作快速、 方便地登录 Windows 登录吗?
ro:Cum să opereze rapid şi uşor se conectează conectare Windows?
pl:Jak działają szybko i łatwo rejestruje identyfikator logowania systemu Windows?
de:Zum Betrieb schnell und einfach protokolliert Windows-Anmeldung?
nl:Gebeurtenislogboeken om snel en gemakkelijk te bedienen Windows-aanmelding?
it:Come far funzionare rapidamente e facilmente log di accesso di Windows?
pt:Como operar rapidamente e facilmente os registros de logon do Windows?
es:¿Cómo utilizar rápidamente y fácilmente registros de inicio de sesión de Windows?
fr:Comment exploiter rapidement et facilement les journaux de connexion Windows ?
Presentation of LogParser
LogParser is a command line utility made available to you by Microsoft from the following address : http://www.microsoft.com/en-us/download/details.aspx?id=24659.
You can also find more details about LogParser à l'adresse suivante (and in french ) : https://technet.microsoft.com/fr-fr/scriptcenter/dd919274.aspx.
An installation in the MSI format file is offered, but once the installation is done, the file LogParser.exe is "portable" (that is, the executable file can be copied and used without installation and without dependence from any workstation using Windows).
This application allows you to generate different information from log in format W files 3C (among other).
This format is used by default by Microsoft IIS (Web and FTP logs ) but other applications also (Mail Enable, to name him ).
The advantage of LogParser is to generate custom reports using a syntax similar to that of the SQL language.
If you host your site on a server Windows (whether it's an offer dedicated or shared )the SQL language you is probably not unknown. Otherwise, you will find examples later in this tutorial to familiarize yourself with SQL syntax and the possibilities that LogParser can offer you.
Utility
Connection logs (regardless of the operating system and whatever the associated service : Web, ftp, mail, et) are too often ignored. Yet they are the first step in a process of search for abnormalities (errors in source code, incorrect links, denial of services, bruteforce, etc. |).
It is consulting on a regular basis historical connection to your server that can take the measurement of abnormal operation or even operation hijacked it and respond quickly.
In addition to the presence of statisti (usage of bandwidth, number of visitors, number of visits, number of mails sent ) such as Awstats or Urchin, generated statistics give only an overview of the different requests made to your website.
With regard to connections to the other services mentioned in the preamble of this article (FTP and SMTP for examp), you have not given encrypted.
In these two cases, among others, LogParser can you be useful.
Prerequis
You will no doubt understand, the prerequisites are few and are limited to :
- LogParser
- the format W connection logs 3C.
We now look to where the connection logs are stored and how to ensure that these logs are in format W 3C.
If you host your site on a shared offer, you can, if you prefer, skip to the next chapter, the configuration of different servers of your hosting you are not accessible.
As a first step, you need to access the IIS management interface via InetMgr which is in %windir%\system32\inetsrv\InetMgr.exe.
In the management of the server, click "Logging". It is in this window that are configured to connect to your server logs :
If you are hosting multiple domain names on a single server, you can store logs of connection of separately where each log file will be created following the domain name or retain only a log to the server file.
You can also, since this window choose the format used to store connection histories. Prefer as much as possible the format W 3C.
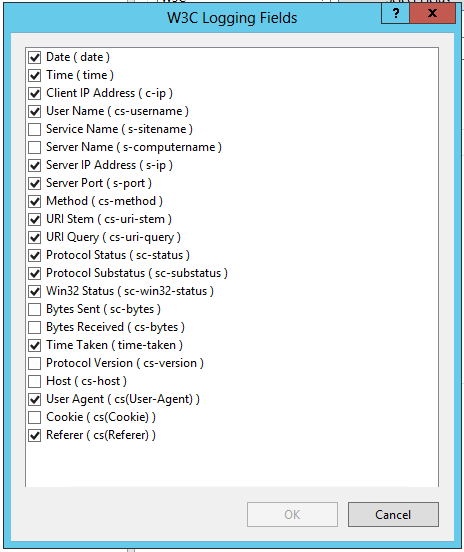
The butt "Select Fields" allows you to make your connection more at least complete logs following the information that you want to check.
Here are the different information that you save in your IIS server connection histories :
You will find details of the various fields proposed via the opposite page : https://technet.microsoft.com/fr-fr/library/cc754702%28v=ws.10%29.aspx.
The second box allows you to set up a rotation of the logs of connection (This comes to define when a new file will be created to store the visits on your site : either in a planned manner, depending on the size of the log file or even not even create different files and everything save a single file ).
Examples of use
Connections are now set file format and location, we will be able to use LogParser.
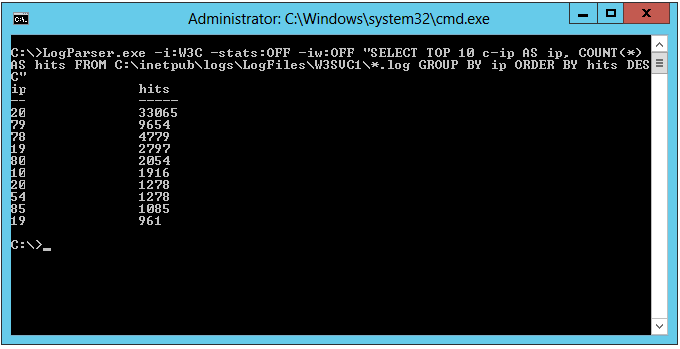
Here is a simple example of using LogParser :
LogParser.exe -i:W3C -stats:OFF -iw:OFF "SELECT TOP 10 c-ip AS ip, COUNT(*) AS hits FROM C:\inetpub\logs\LogFiles\W3SVC1\*.log GROUP BY ip ORDER BY hits DESC"
Some explanations are necessary :
- the opt "-i:W3C" allows to force the reading of connection files in format W 3C
- the opt "-stats:OFF" to disable statistics generated by LogParser (number of driven records, number of results generated by the query, the query execution time )
- the opt "-iw:OFF" to disable error messages encountered by LogParser in reading the files
- "
SELECT TOP 10 c-ip AS ip, COUNT(*) AS hits FROM C:\inetpub\logs\LogFiles\W3SVC1\*.log GROUP BY ip ORDER BY hits DESC" is the query in the SQL form : It allows you to browse all the .log files in the directory C:\inetpub\logs\LogFiles\W3SVC1\ and select the 10 IP address of the most visits to connection logs that are traversed (via the association "TOP 10", de "GROUP BY ip" and "ORDER BY hits DESC").
To make a comparison with a SQL, the directory of log files database (which may be multiple, concatenated with a comma, is the name of the table, the name of "Field" (V are preceding paragraph in the connections log configuration ) corresponds to the field in the table.
Here is the result obtained following our use LogParser and the SQL query passed as an argument (the IP addresses of visitors to our site have been masked ) :
Practical ca
You can from LogParser do a lot of different things : create scripts that implement a policy of Security on your server if a visitor logs accesses to your site more than X times in a time interval, generate graphs based on various statistics (via options "-o:chart" et "-chartType:barstacked" for exampl - requires the installation oOffice Chart Web Component However -), what are the pages that generate the most traffic to your site, etc.
Go further with LogParser
This tutorial is just a preamble to use LogParser. If you want to go further in the use of this application and especially at the level of the SQL queries that you can use with the utility, LogParser, you will find examples via the links below :
- http://blogs.iis.net/carlosag/archive/2010/03/25/analyze-your-iis-log-files-favorite-log-parser-queries.aspx
- http://logparserplus.com/Examples
This article seemed you to be u ?

Enable comment auto-refresher