Difference between revisions of "Securing my mutualized hosting"
(Created page with "<span data-link_translate_fr_title="Sécuriser mon hébergement mutualisé" data-link_translate_fr_url="Sécuriser mon hébergement mutualisé></span>:fr:Sécuriser mon hé...") |
|||
| Line 21: | Line 21: | ||
==Sending mail== | ==Sending mail== | ||
<br /> | <br /> | ||
| − | So that sending email is only authorized from your shared hosting for your domain name, we invite you to set up an SPF field in the DNS zone of your domain name: https://fr-wiki.ikoula.com/ | + | So that sending email is only authorized from your shared hosting for your domain name, we invite you to set up an SPF field in the DNS zone of your domain name: https://fr-wiki.ikoula.com/fr/Qu%27est_que_le_SPF_%3F <br /> |
If an e-mail is attempted with your domain name via an unauthorized server, it will be directly put in SPAM or blocked according to the security policy of the destination e-mail server. | If an e-mail is attempted with your domain name via an unauthorized server, it will be directly put in SPAM or blocked according to the security policy of the destination e-mail server. | ||
| − | As a reminder, you can manage the DNS zone of your domain name like this: https://fr-wiki.ikoula.com/fr/ | + | As a reminder, you can manage the DNS zone of your domain name like this: https://fr-wiki.ikoula.com/fr/Comment_administrer_ma_zone_DNS_depuis_mon_PLESK |
<br /> | <br /> | ||
==Password== | ==Password== | ||
Latest revision as of 14:20, 30 September 2022
fr:Sécuriser mon hébergement mutualisé en:Securing my mutualized hosting es:Asegurar mi alojamiento compartido
Introduction
You will see in this article, the different possibilities to secure your shared hosting.
Sending mail
So that sending email is only authorized from your shared hosting for your domain name, we invite you to set up an SPF field in the DNS zone of your domain name: https://fr-wiki.ikoula.com/fr/Qu%27est_que_le_SPF_%3F
If an e-mail is attempted with your domain name via an unauthorized server, it will be directly put in SPAM or blocked according to the security policy of the destination e-mail server.
As a reminder, you can manage the DNS zone of your domain name like this: https://fr-wiki.ikoula.com/fr/Comment_administrer_ma_zone_DNS_depuis_mon_PLESK
Password
Use complex passwords whether for access to your mailboxes, FTP access, access to your Ikoula account, access to the administration interface of your CMS, access to your database.
You can use this site to generate secure passwords: https://www.motdepasse.xyz/
- To modify your FTP passwords, you can do so via the FTP access management of your Plesk interface: https://fr-wiki.ikoula.com/fr/Acc%C3%A9der_%C3%A0_la_gestion_de_mes_comptes_FTP
- To change your mailbox passwords, you can do so via the management of your mailboxes on your Plesk interface: https://fr-wiki.ikoula.com/fr/Acc%C3%A9der_%C3%A0_la_gestion_de_mes_bo%C3%AEtes_mails
- To change the password to your Ikoula account, you can do it like this: https://fr-wiki.ikoula.com/fr/Comment_changer_son_mot_de_passe
- To change your database user password, you can do so through your Plesk interface.
Keeping your CMS up to date
If you use a CMS, we invite you to keep it up to date, in fact most of the hacking comes enormously from CMS flaws:
- You can consult this site which lists the various Wordpress vulnerabilities: https://www.cvedetails.com/vulnerability-list/vendor_id-2337/product_id-4096/
- Joomla: https://www.cvedetails.com/vulnerability-list/vendor_id-3496/product_id-16499/Joomla-Joomla-.html
- Prestashop: https://www.cvedetails.com/vulnerability-list/vendor_id-8950/Prestashop.html
These flaws are usually corrected in the proposed updates.
Here are links that explain how to update the different CMS:
- For Wordpress, you can update it like this: https://codex.wordpress.org/fr:Mettre_a_Jour_WordPress
- For Joomla: https://docs.joomla.org/J3.x:Updating_from_an_existing_version/en
- For Prestashop: https://addons.prestashop.com/fr/migration-donnees-auvegarde/5496-.html?pab=1&
Plugins/themes
Use trusted plugins/themes, for this we invite you to use official sites to obtain your plugins/themes, for example for Wordpress, you must also keep them up to date: https://fr.wordpress.org/themes/ , https://fr.wordpress.org/plugins/
We also invite you to check the ratings/reviews of the plugins to see if other users have encountered problems with them.
Malware Scan
You have the possibility to scan your website in order to detect malware present via online tools such as: https://sitecheck.sucuri.net/
Sending mail from an unauthorized script
If an email was sent from a script, you can identify the script in question in the header of the email (https://fr-wiki.ikoula.com/fr/R%C3%A9cuperer_les_headers_de_mes_courriers) using the field : X-PHP-Originating-Script: scriptname.php , then rename/delete it accordingly so that it no longer runs.
Example of an email that was sent from a php script:
Return-Path: <sitename@server.example.com> Received: from [x.x.x.x] by example.com (MTA v5/:PGFiZWxsZW5AbWFuYWdlZHNoYXJlZDIuYXJyb3dxdWljay5uZXQ_) with SMTP id <20130717204350103198600015> for <example@example.com>; Wed, 17 Jul 2013 20:43:50 -0500 (CDT) (envelope-from sitename@server.example.com, notifiable emailhost server.example.com) Received: by server.example.com (Postfix, from userid 1040) id 888C414E32F; Wed, 17 Jul 2013 20:27:09 -0500 (CDT) To: example@example.com Subject: Order Detail X-PHP-Originating-Script: 1040:kka3f2.php From: "First-Class Mail Service" <test@example.com> Reply-To: "First-Class Mail Service" <test@example.com> Mime-Version: 1.0 Content-Type: multipart/alternative;boundary="----------137411082951E7446D85129" Message-Id: <20130718012709.888C44414E32F@server.example.com> Date: Wed, 17 Jul 2013 20:27:09 -0500 (CDT)
We are therefore going to delete or rename the *kka3f2.php* script so that it no longer runs.
Securing your Wordpress installation
For wordpress, you can secure your installation like this: https://fr-wiki.ikoula.com/fr/Comment_s%C3%A9curiser_et_maintenir_son_installation_Wordpress
Encrypt exchanges between client and server
Encrypt exchanges between client and server by setting up an SSL certificate, you can use 'Let's Encrypt' on hosting with Plesk 12.5: https://fr-wiki.ikoula.com/fr/Comment_installer_un_certificat_Let%27s_encrypt_depuis_mon_acc%C3%A8s_Plesk_%3F
This allows "sniffers" not to be able to see what passes between the browser (client) and the server and therefore not to recover essential information such as passwords, important data.
We also offer SSL certificates at this address: https://www.ikoula.com/fr/certificats-ssl
PHP Version
Use the latest versions of PHP in order to overcome the various security vulnerabilities, you can change the PHP version of your hosting like this: https://fr-wiki.ikoula.com/fr/Comment_changer_la_version_de_PHP_pour_mon_h%C3%A9bergement
You can also consult this article to learn how to fight PHP flaws: https://www.lije-creative.com/script-php-faille/
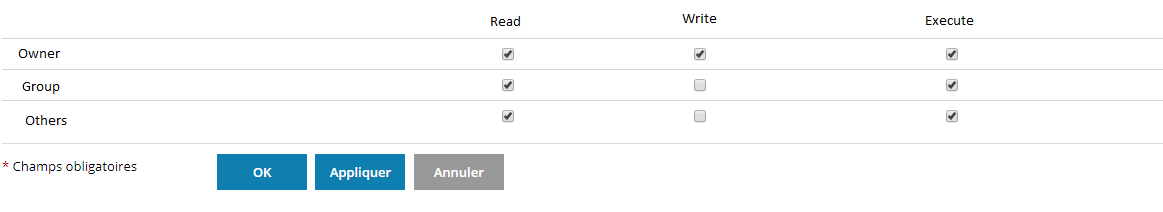
Permissions
It is strongly advised not to use full rights for your files on your hosting (777), by default we advise you to use rights in '755' or '705' like this (755):